


Compact, discreet and precise, Apple-branded AirTag GPS beacons are the target of malicious hijacking. Some people find themselves tracked in spite of themselves…
This is followed by acts of harassment, or various forms of trafficking such as car theft.
Originally, the AirTag – which costs about thirty euros – is a small bluetooth beacon dedicated to heads in the air. We hang it on his keys, we slip it into his bag, and finish the panic before going out when we forgot where these essentials were stored.
With one click, you can ask the AirTag, which is the size of a two-euro coin, to emit a sound, which makes it easy to find it. If he is too far away, you can find him via the “Itinerary” tab, and be guided to him. Apple specifies on its website that the tool also allows you to find your Apple devices, or “not to lose sight of your loved ones”. The problem is that this last use has been largely diverted…
An AirTag hidden on the wheel of his car
On Twitter, Ashley tells for example in December 2021 something “rather terrifying” that happened to her. While she was in a bar, someone would have taken the opportunity to slip an AirTag on her car.
https://twitter.com/Sega__JEANAsis/status/1472198123506257937
“It was two o’clock in the morning and I was driving on a road where there were no cars, but I kept getting an alert.”
These notifications, of which she took a screenshot, visible below, tell her that an AirTag is following her.
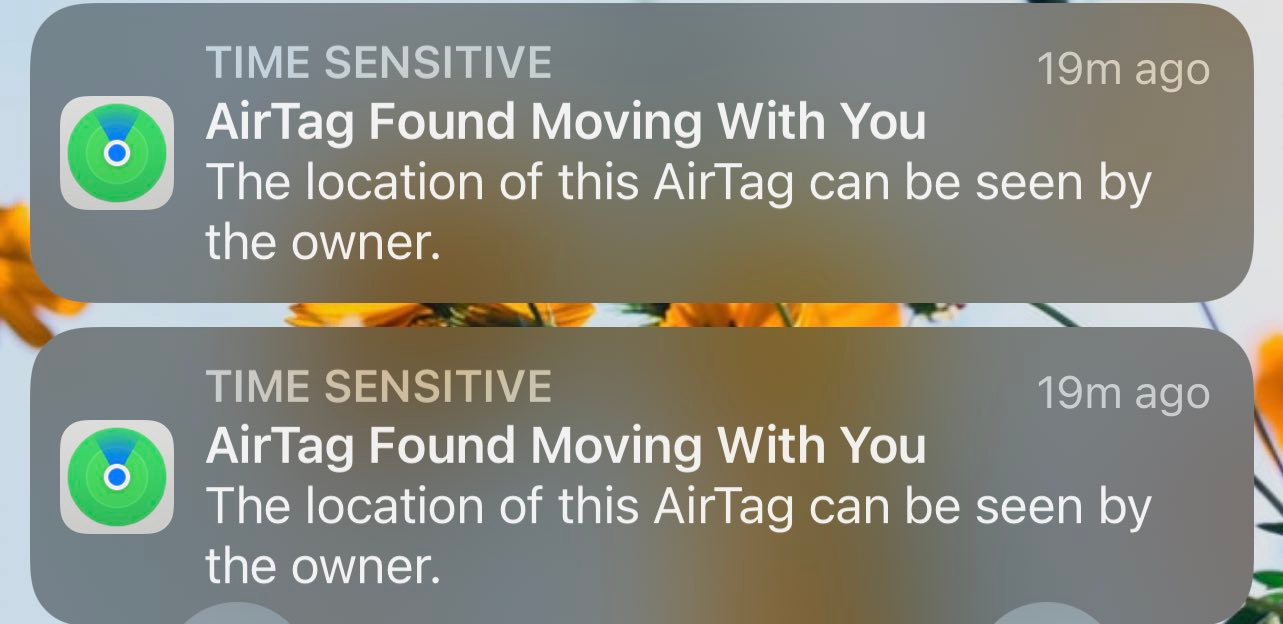
After multiple searches, and a night of anguish far from home, she finally finds one, at the level of her front wheel.
Testimonials like Ashley’s are pouring in on social media, including Twitter and TikTok. Most of the time, women tell how they were geolocated without their knowledge by means of an AirTag.
Car theft or harassment: what are the risks?
There are several types of malicious hijacking. In Canada, AirTags have been hidden in luxury cars, in order to locate the homes of their owners… and steal them quietly afterwards.
They can also be used to track a person’s movements. At the BBC, Eva Galperin, head of cybersecurity issues at the Electronic Frontier Foundation (EFF), ironically explained that it was a “perfect tool for harassment”.
This follow-up can be carried out by a stranger, as was obviously the case for Ashley, but also by a relative, in the context of domestic violence. As Numerama noted, it would even be the latter “who represent the greatest risk”.
It has been a long time since the so-called “cyberviolence” (which concerns 9 out of 10 women victims of domestic violence, according to the Hubertine Auclert Center) is no longer limited to reading text messages without the agreement of the other. Tracking and spying on the partner is part of the means of control used. This data can be used to monitor but also manipulate the victim. Several such cases have been reported to authorities in the United States with AirTags.
Should we be afraid of AirTags?
Of course, AirTags are not the only tools that allow this type of abuse. There are many dedicated applications (spyware), applications diverted from their basic use (parental control apps in particular), or even features included on smartphones such as geolocation sharing, which can be activated more or less discreetly without a person’s knowledge.
A real business has been created around this gloomy market, told Le Monde in an investigation.

The specificity of AirTags, however, is to be cheap and accessible to the general public, but also to offer an accurate and updated location on a regular basis. To locate them, Apple uses its “Locate” network. In concrete terms, this means that all iPhones, iPads or computers of the brand become relay points, specifying geolocation. In a densely populated space, a shopping center, a restaurant or other, the location will therefore be a priori more updated and more reliable.
Apple deploys security features to prevent abuse
To remedy these abuses, Apple has implemented devices such as the text notification system when a beacon follows us.
This notification is only visible on smartphones or tablets of the brand, but it is possible to install a dedicated application on Android – developed by Apple -, which is called Tracker Detector. On iPhone, one can also perform a check in the “Locate” app, by selecting “Devices”.
The AirTag is also programmed to ring if it is too far from its owner for a long time, thus warning people who do not have a smartphone, or an Android smartphone. This period has been shortened from three days to a range of between 8 and 24 hours from June 2021. It seems, however, that the ring, of 60 decibels, is not very audible in the event that the AirTag is stuck on a car. Some also manage to disable it. On YouTube, tutorials reach several tens of thousands of views, even if the comments suggest that it would be mainly the assurance of discretion for a theft of equipment for example (on a bike, etc.).

Now that you know what are the different ways to detect an AirTag that follows you, we also invite you to read our tutorial on Better Web, dedicated to the detection of other means of surveillance, such as spyware mentioned above.
Read also: How do I know if someone geolocates me via my smartphone?
We also list emergency numbers to contact if you ever experience this type of cyberviolence. Be aware that all AirTags are equipped with an NFC chip that can be read with any smartphone, and which indicates the procedure to follow in case of problems. In general, if you find one of these small objects for no reason at the bottom of your bag or on your car, it is best not to go directly home and instead take it to a police station. It is sometimes possible to find their owner. The same applies to spyware applications.